※1 当社調べ ※2 SECCON CTF 13 Finals:国内1位 ※3 2023年~2025年 DEF CON Cloud Village CTF:世界1位
このようなお悩みはございませんか?
-
各部署で次々にwebサイト(ドメイン)を立ち上げていて管理しきれていない。
-
一部の重要サイトをたまにしか診断できていない。本当はすべてやりたいが手間も時間もお金もかかる…
-
診断結果が出たあとの運用がいつもうまく行かない。
-
各部署の脆弱性対応状況を手間なく総合管理したい。

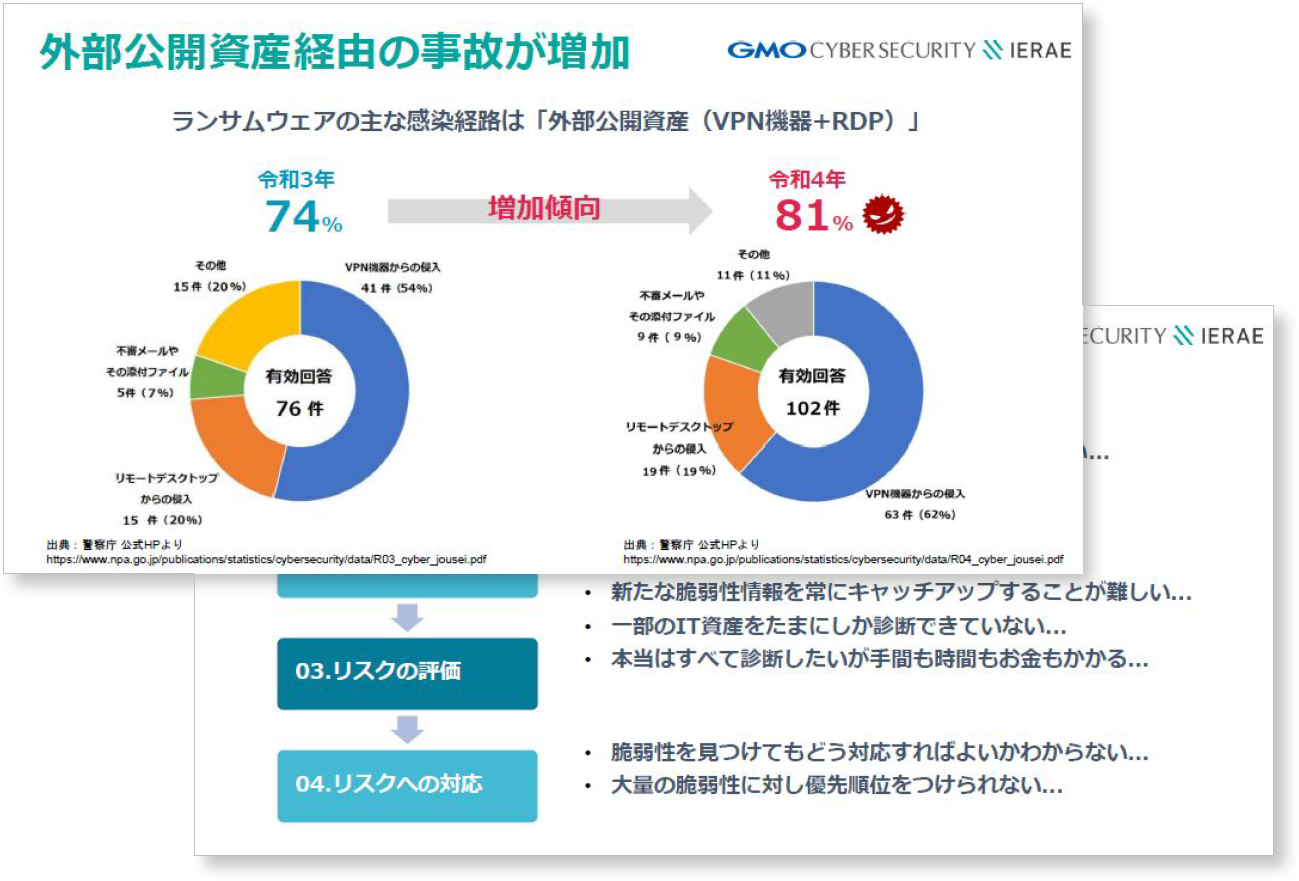
ネットde診断ならサイバー攻撃の対象となりうるIT資産を可視化し、組織全体の脆弱性対策ができます!
-
手間なくwebサイト(ドメイン)の洗い出しと管理ができる!
-
毎回ログインする必要はなく、問題があるときのみアラート検知が可能。
1サイトあたり3000円で診断できるコスパの良さ! -
専門家の運用サポートで優先度や対応方針が分かる!(イエラエアドバイザリーサービス)
-
多くのサイトを定期的に自動で診断。
各サイトの対策状況がわかる!
2分で解説ASMの必要性とネットde診断でできること
診断フロー
GMOサイバー攻撃ネットde診断は、ツールとコンサルティングで誰でも簡単にASMを実現します。

- 攻撃面の発見
- 攻撃面の情報収集
- リスクの評価
- リスクへの対応

- 攻撃面の発見
- GMOサイバーセキュリティ byイエラエのホワイトハッカーが攻撃者目線で外部公開されている自社のIT資産を棚卸します。
- 攻撃面の情報収集
- ツールによる定期診断で週に1回、脆弱性情報を自動で収集し、必要に応じて随時の診断も可能です。
- リスクの評価
- 影響度をもとにツールが脆弱性を自動でランク付けし、優先度をセキュリティコンサルタントがアドバイスします。
- リスクへの対応
- ツールに表示された対応方法を実行します。
不明点はセキュリティコンサルトが対応サポート!
はじめての方でも使いやすい国産ASM
-
国産ならではの使いやすさ
ASMツールは海外製が多く、言語の障壁や不自然な翻訳に悩まされることがあります。ネットde診断は国産であるため分かりやすく使いやすいのが特徴です。
-
セキュリティをトータルサポート
セキュリティ分野の中でも様々な領域の専門家が大集結。診断して終わりではなく、その後のサポートまで貴社のビジネスを幅広くお守りいたします。
-
圧倒的なコストパフォーマンス
GMOインターネットグループの大規模な基盤を活用することでシステムコストを大幅に削減。他社には真似できないコストパフォーマンスを実現しました。1サイトあたり3,000円で診断できます。
サービス紹介・ASM解説資料
Webサイト、ドメイン、VPNといったIT資産の管理者様へ向けて、ASMの基礎知識やツール導入のメリットを解説する資料を無料でご提供しています。
主な診断範囲
GMOサイバー攻撃ネットde診断は、ツールとコンサルティングで誰でも簡単にASMを実現します。
-
Webアプリケーション診断
クロスサイトスクリプティングやSQLインジェクションなどWebアプリケーションに潜む脆弱性を診断します。
- SQLインジェクション
- OSコマンドインジェクション
- バッファオーバーフロー
- ディレクトリトラバーサルなど
-
ネットワーク診断
診断対象ネットワークに存在するサーバやネットワーク機器等に、既知の脆弱性や設定の不備等によるセキュリティ上の問題点がないかを診断します。
- メールサーバ
- Webサーバ
- SSHサーバ
- FTPサーバなど
- VPN機器
-
CMS診断
本体やプラグイン、テーマのバージョン情報などから既知の脆弱性の有無を確認します。
WordPress、 EC-CUBE など対象製品は随時追加中。
詳しく知りたい方は診断範囲一覧をご確認ください
その他主な機能のご紹介
昨日、脆弱性でなかったものが今日、脆弱性になる可能性があるネットde診断は豊富な機能で大事なサイトをお守りします。
-
- 外部公開資産の棚卸
- 社名や製品名、ドメイン名などの起点情報をもとに、関連する外部公開資産を棚卸します。
-
- ダークウェブ
ID/パスワード流出監視 - メールアドレスやパスワードなどのアカウント情報の漏えい有無を確認できます。
- ダークウェブ
-
- パッシブスキャン
- 通常のアクセスの範囲内で、対象システムに負荷をかけずに脆弱性を検出します。
-
- アクティブスキャン
- 対象に影響を与えない範囲で疑似的な攻撃通信を行い、応答結果をもとに詳細に脆弱性を検出します。
-
- 外部公開資産の一元管理
- ドメインやIPアドレスの一覧をダッシュボードで管理します。新規に検出した資産は適宜追加可能です。
-
- アドバイザリーサービス
- 発見した問題の対策やトリアージ(優先度や対応方針)に関してご相談が可能です。
-
- レポート発行
- 診断結果レポートはPDFやCSV形式でエクスポートが可能です。
-
- ロール管理
- 子会社や部署ごとにダッシュボードを作成し、アクセス権限を分けて管理することが可能です。
-
- アラートメール
- 緊急度の高い脆弱性が発見された場合、メールで通知をすることが可能です。
※掲載している機能は一部です。その他詳しい機能はお問い合わせください。
料金プラン
導入事例

- 事業部ごとに脆弱性診断の実施状況や基準がバラバラ
- サービスが多く、診断前の事前準備や調整の工数負荷が膨大
- 診断頻度が少なく、最新の脆弱性対策状況のキャッチアップが困難
- 統一基準による脆弱性診断によりガバナンスを強化
- 負荷をかけずに全社に対して脆弱性診断を実施
- 定期診断により最新の脆弱性対策状況を定期監視
IT資産管理や脆弱性管理はなぜ必要?
昨今、クラウドサービスやホスティングサービスの普及により、サービスをインターネット上に簡単に公開することができるようになりました。
一方で、各サービス事業部門や海外子会社が独自にこれらを設置してしまうことで、情報システム部門やセキュリティチームが把握できていないWebサイトやネットワーク機器などのIT資産が増加しています。これらは、セキュリティ対策が不十分な状態で放置されていることも多く、サイバー攻撃の入り口として狙われるリスクが高くなっています。
ASM(アタックサーフェスマネジメント)は、インターネットからアクセス可能なIT資産の情報を調査し、それらに存在する脆弱性を継続的に評価する取り組みです。
GMOサイバー攻撃ネットde診断 ASMではOSINT(Open Source Intelligence)手法を活用した外部公開資産の把握や、定期的なセキュリティ診断、セキュリティコンサルタントによるアドバイザリーサービスを通じて、はじめてのASM(攻撃面に対する適切なリスク管理)を支援します。
経産省が推奨するASM
経済産業省は、サイバー攻撃から自社のIT資産を守るための手法として注目されている「ASM(Attack Surface Management)」について、自社のセキュリティ戦略に組み込んで適切に活用してもらえるよう、ASMの基本的な考え方や特徴、留意点などの基本情報とともに取組事例などを紹介した、「ASM導入ガイダンス」を公開しました。
ネットde診断はこのASMにカテゴライズされるツールとなります。
※経産省のガイドラインはこちら(外部リンク)
定期診断が必要な理由
-
日々、新たな脆弱性が発見されている
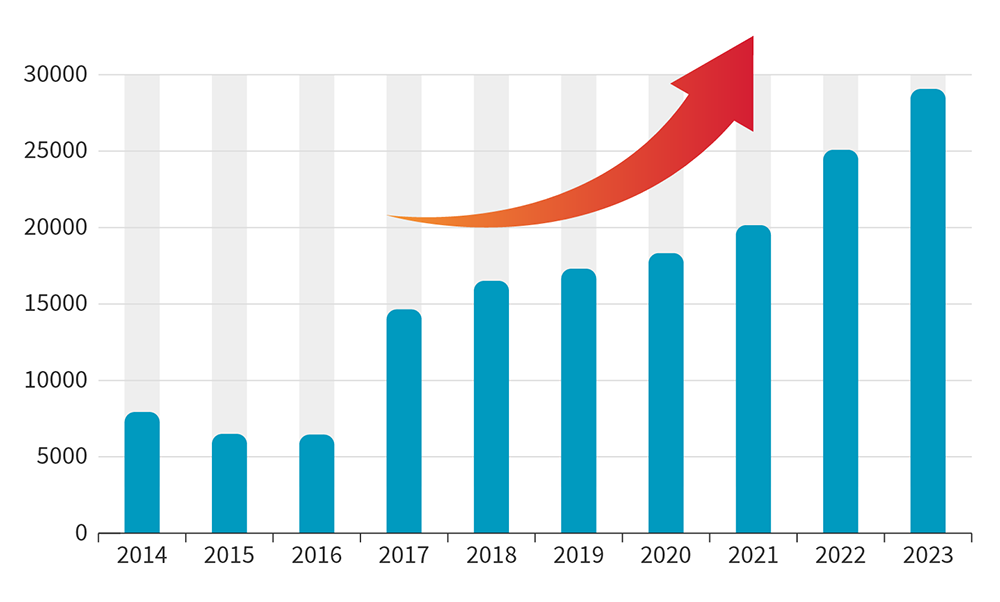
2023年に登録された脆弱性は29,066件以上。
つまり1日あたり79件の脆弱性が発見されています。
出典元 -
システム改修/更新により
新たな脆弱性が発生する可能性がある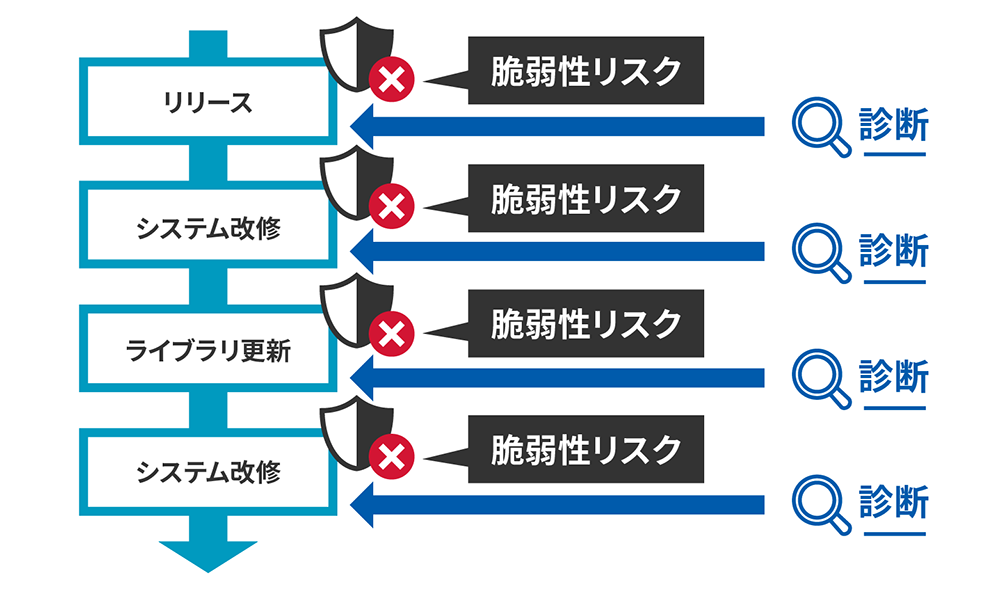
Webアプリのリリース後も、ライブラリの更新や改修の度に脆弱性リスクは発生します。
ベストは毎日、最低でも週1回〜月に1回の診断を推奨します
初めての方にも簡単、手軽にセキュリティを届けたい

ネットde診断 ASM は、開発者が感じた「いくら高いセキュリティを提供できるプロダクトでも、ユーザーに複雑な操作を求めてしまうと利用されない、結果として何もセキュリティが向上しない」という課題を解消すべく、ワンクリックで誰でも簡単に使えるものを目指して開発されました。
開発者インタビューはこちら「情報セキュリティサービス基準適合サービスリスト」登録済
当社のGMOサイバー攻撃ネットde診断
は経済産業省の定める情報セキュリティサービス基準に適合したサービスとして「情報セキュリティサービス台帳」に登録されています。
サービス名:脆弱性診断サービス[ペネトレーションテスト(侵入試験)サービス含む]
登録番号:019-0004-60

019-0004-60
各種ガイドラインへの対応を推進
各種ガイドラインに基づいた診断を行うため、評価基準をアップデートしています。
-
情報セキュリティサービス基準
経済産業省が情報セキュリティサービスに関する一定の技術要件及び品質管理要件を示し、品質の維持・向上に努めている情報セキュリティサービスを明らかにするため設けた基準。
-
PCI DSS ASV認定
クレジットカード業界のセキュリティ基準であるPCI DSSに準拠した診断を行う資格。
-
安全なウェブサイトの作り方
IPA 独立行政法人 情報処理推進機構による、Webアプリケーションのセキュリティ運用と安全性向上の為の取り組み。
-
OWASP TOP10
OWASPがWebセキュリティ上多発する脅威の中で、その危険性が最も高いと判断された項目。
-
政府情報システムにおける
脆弱性診断導入ガイドラインデジタル庁による、脆弱性診断を効果的に導入するための基準及びガイダンス。
対応内容の詳細や機能についてはこちら
当社の実績
-
診断実績
360万件 -
継続率
98% -
CTF優勝回数※1
9回 -
CVE申請数※2
245件
※1 CTF…サイバーセキュリティのスキルを競うハッキングコンテスト
※2 CVE申請⋯WindowsやMacOSをはじめとするOSやソフトウェアの脆弱性を発見し申請
よくある質問
-
ドメインとはなんですか。
-
ドメインとはインターネット上の住所のことでWebサイトを判別する独自の情報です。GMOサイバーセキュリティbyイエラエの場合「gmo-cybersecurity.com」が企業のドメインになります。
-
LAN内のサイト(プライベートIPアドレスを持つサーバ)は診断可能ですか。
-
診断できません。
現在はグローバルIPアドレスを持つサイトの外部からの診断のみ可能です。
-
SQLインジェクションやクロスサイトスクリプティングなどの脆弱性は検知できますか。
-
検知可能です。システムに対して負荷をかけずに確認できる範囲で検知します。
-
脆弱性診断によってサーバが落ちる可能性はありますか。
-
リソースの問題なく運用できているサーバであれば落ちる可能性はありません。
-
脆弱性診断ではどのような結果が得られますか。
-
意図せず不要なポートが開いていないかや、攻撃方法や影響が公開されている「既知の脆弱性」の有無などがわかります。
検出された脆弱性の影響については管理画面上の診断レポートにて確認できます。
資料ダウンロード

自社のWebサイトの管理者様や、クライアントのWebサイト管理を行っているご担当者様に向けて、ASMの基礎知識からツール導入のメリットを解説する資料を提供しています。
資料内容
- ASMツールが必要な理由
- ネットde診断 for ASM でできること
- 料金表
- オプション詳細
- よくあるご質問
















