GMO Attack Surface Management
This ASM (Attack Surface Management) tool helps you manage IT assets and assess vulnerabilities that could be targeted by attackers from the internet.


*1 Source: Our company's research. *2 SECCON CTF 13 Finals:1st Place in Japan *3 DEF CON Cloud Village CTF: 1st Place in the world (2023-2025)
Do you have any of these concerns?
-
Each department is launching new websites (domains) one after another, making it increasingly difficult to manage them all.
-
We're only able to diagnose some of our important sites occasionally.We'd like to diagnose all of them, but it requires significant time, effort, and cost.
-
We often find that the implementation of solutions after a diagnosis doesn't go smoothly.
-
We want to manage the vulnerability response status of each department in an integrated manner without any hassle.

Identify and secure your IT assets vulnerable to cyberattacks with "GMO Attack surface Management"! Our solution provides comprehensive vulnerability management for your entire organization.
-
Manage your websites (domains) effortlessly.
-
Receive automated alerts only when issues arise—no need for constant logins. For just 3,000 yen per site, you get exceptional value for your website diagnosis.
-
Our expert operational support helps you understand the priority and response policy.
-
We automatically perform regular diagnostics on many sites. You can easily track the status of measures for each site.
Operational Flow
GMO Attack Surface Management provides tools and consulting that make ASM easy for anyone to implement.

- Discovering the attack surface
- Gathering attack surface information
- Assessing risk
- Responding to risks

- Discovering the attack surface
- GMO Cybersecurity by Ierae’s white hat hackers will identify your company’s exposed IT assets (shadow IT) from an attacker’s perspective.
- Gathering attack surface information
- Automated weekly scans identify vulnerabilities. On-demand scans are also available.
- Assessing risk
- The tool automatically ranks vulnerabilities based on their impact, and security consultants provide advice on prioritization.
- Responding to risks
- Follow the instructions in the tool.
If you have any questions, our security consultants will assist you!
Easy-to-use domestic ASM even for beginners
-
The clarity unique to Japanese-made products
Many ASM tools are made overseas and often encounter language barriers and unnatural translations. GMO Attack surface Management is made in Japan, so it is easy to understand and use.
-
Total security support
We have assembled a team of experts from various fields within the security industry. We not only diagnose problems but also provide comprehensive support to protect your business.
-
Unparalleled cost-effectiveness
By utilizing the large-scale infrastructure of the GMO Internet Group, we have significantly reduced system costs. We have achieved cost-effectiveness that cannot be matched by other companies. We offer site diagnostics for just 3,000 yen per site.
Main diagnostic range
GMO Attack Surface ManagementTools and Consulting: Anyone Can Easily Achieve ASM.
-
Web Applications Assessment
We diagnose vulnerabilities in web applications, such as cross-site scripting and SQL injection.
- SQL Injection
- OS Command Injection
- Buffer Overflow
- Directory traversal etc.
-
Network Diagnostics
We diagnose whether there are any security issues due to known vulnerabilities or improper configurations on the servers and network devices on the target network.
- Mail Server
- Web Server
- SSH Server
- FTP server, etc.
- VPN Devices
-
CMS Diagnosis
We check for known vulnerabilities from version information of the main body, plugins, and theme.
Target products, such as WordPress and EC-CUBE, are constantly being added.
Other main features
What wasn't a vulnerability yesterday could be a vulnerability today.GMO Attack Surface Management has a wide range of functions to protect your important sites.
-
- External Asset Inventory
- Using seed entities like company names, product names, and domain names, this function discovers and catalogs all associated public-facing assets.
-
- Dark Web Credential Monitoring
- You can check if your account information has been compromised.
-
- Passive Scan
- Detects vulnerabilities by analyzing normal user traffic without affecting the performance of the target system.
-
- Active Scan
- Detects vulnerabilities in detail by sending simulated attack traffic and analyzing the responses, conducted in a safe manner that avoids impacting the target system.
-
- Centralized External Asset Management
- Manage all your domains and IP addresses on a single dashboard. You can easily add any newly discovered assets.
-
- Advisory Service
- Get expert advice on fixing and prioritizing security findings. We help you build an effective remediation strategy.
-
- Report Issuance
- Scan reports can be exported in PDF and CSV formats.
-
- Role Management
- You can create separate dashboards for each subsidiary or department and manage their access permissions individually.
-
- Alert email
- You can receive email notifications for newly discovered, critical vulnerabilities.
*This is only a portion of the features listed.For other detailed functions, please contact us.
料金プラン
Why are IT asset management and vulnerability management so important?
The rise of cloud and hosting services has made it easier than ever to establish an online presence. However, this ease of access has also led to a proliferation of unmanaged IT assets. As various departments and subsidiaries deploy their own systems, IT infrastructures become increasingly complex. This often results in "shadow IT" - websites, network devices, and other assets that fly under the radar of IT and security teams. Without proper management and security measures, these unknown assets become easy targets for cyberattacks, significantly increasing your organization's risk.
ASM (Attack Surface Management) provides a proactive approach to cybersecurity by continuously identifying and assessing vulnerabilities in your internet-facing IT assets.
simplifies and streamlines your ASM efforts. We combine the power of OSINT (Open Source Intelligence) techniques, regular automated security assessments, and expert consultation to provide you with a comprehensive understanding of your attack surface and guide you in implementing effective risk mitigation strategies.
Government-Recommended Security Standard
The Ministry of Economy, Trade and Industry (METI) recognizes the importance of ASM and has issued guidelines for its implementation as a vital measure for protecting corporate IT assets from cyberattacks. These guidelines provide a comprehensive overview of ASM, including its fundamental concepts, key characteristics, implementation considerations, and real-world case studies.
GMO Attack surface Management is a tool that falls under the ASM category.
* METI guidelines can be found here (external link)
Why Regular Checkups are Necessary
-
New vulnerabilities are discovered every day
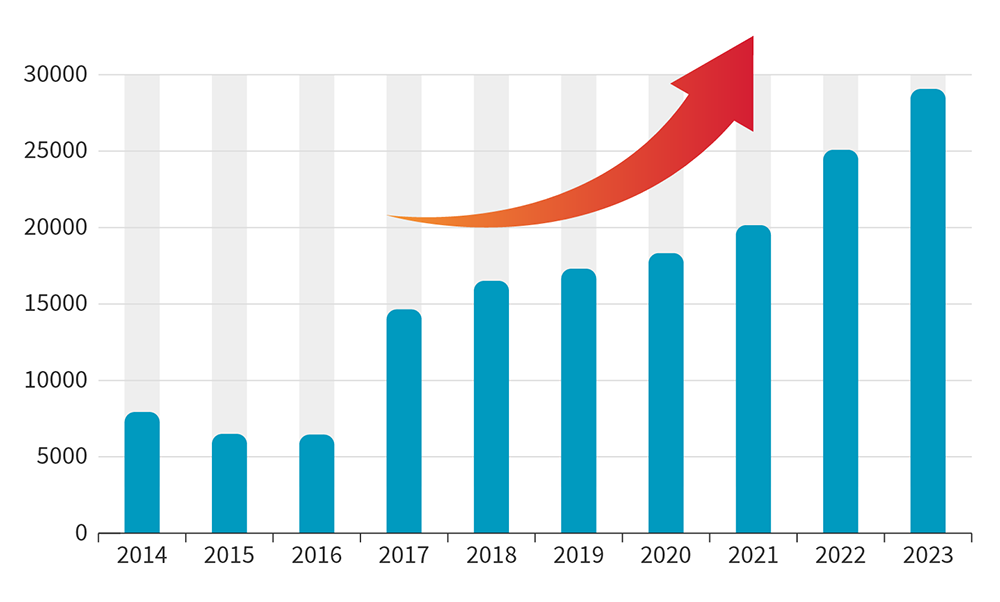
More than 29,066vulnerabilities were registered in 2023.
This means that 79vulnerabilities discovered every day.
Source -
Due to system repairs/updates
New vulnerabilities may emerge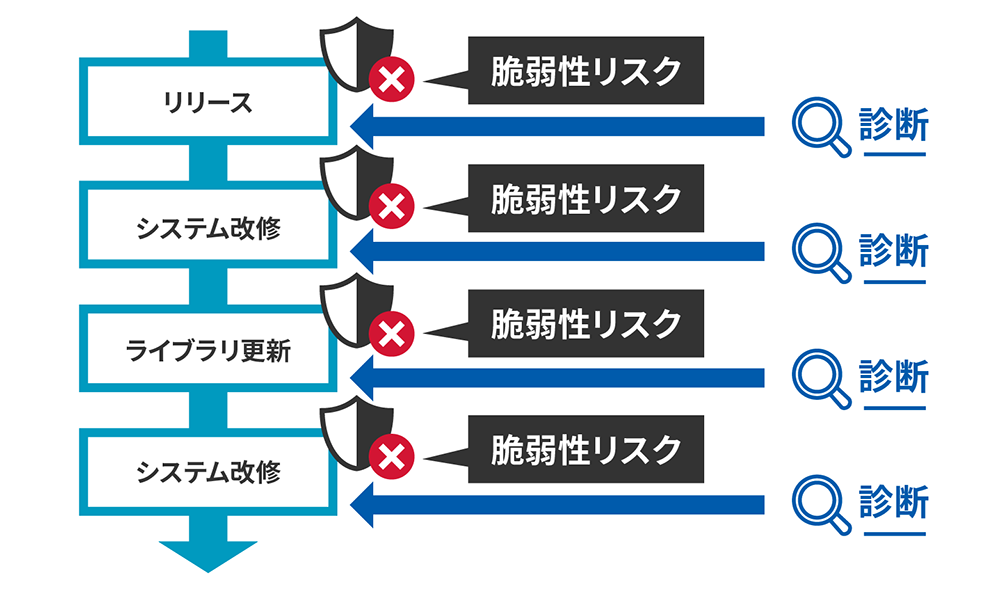
Even after a web application is released, the risk of vulnerabilities arises every time the library is updated or modified.
at the very least, a weekly or monthly diagnosis is necessary.
We want to provide security that is simple and easy even for first-time users.

GMO Attack Surface Management was developed to be easy for anyone to use. The developers created a solution that can be implemented with just one click, addressing a key challenge: No matter how strong a security product is, it won't improve security if it's too complicated to use.
Read the developer interview herePromoting compliance with various guidelines
We are continuously updating our evaluation criteria to align with various industry guidelines.
-
Information Security Service Standards
The Ministry of Economy, Trade and Industry established these standards to define technical and quality control requirements for information security services, highlighting efforts to maintain and improve service quality.
-
PCI DSS ASV Certification
Qualification to perform diagnostics in compliance with PCI DSS, the security standard for the credit card industry.
-
How to create a secure website
An initiative by the Information-Technology Promotion Agency, Japan (IPA) to improve the security and safety of web applications.
-
OWASP TOP 10
The highest-risk items among the web security threats provided by OWASP.
-
Guidelines for Introducing Vulnerability Assessment in Government Information Systems
Standards and guidance for effectively introducing vulnerability assessments by the Digital Agency.
Click here for details on the content and functions
Our track record
-
Diagnostic tests performed
3.6million -
Retention rate
98% -
CTF wins*1
9 -
CVE submissions*2
230
*1 CTF: A hacking contest to test cybersecurity skills
*2 CVE submission: Submitting a submission to discover vulnerabilities in operating systems and software, including Windows and MacOS
FAQ
-
What is a domain?
-
Can sites within a LAN (servers with private IP addresses) be diagnosed?
-
Can vulnerabilities such as SQL injection and cross-site scripting be detected?
-
Is there a possibility that vulnerability assessment will cause the server to crash?
-
What kind of results can I expect from a vulnerability assessment?
Download eBook
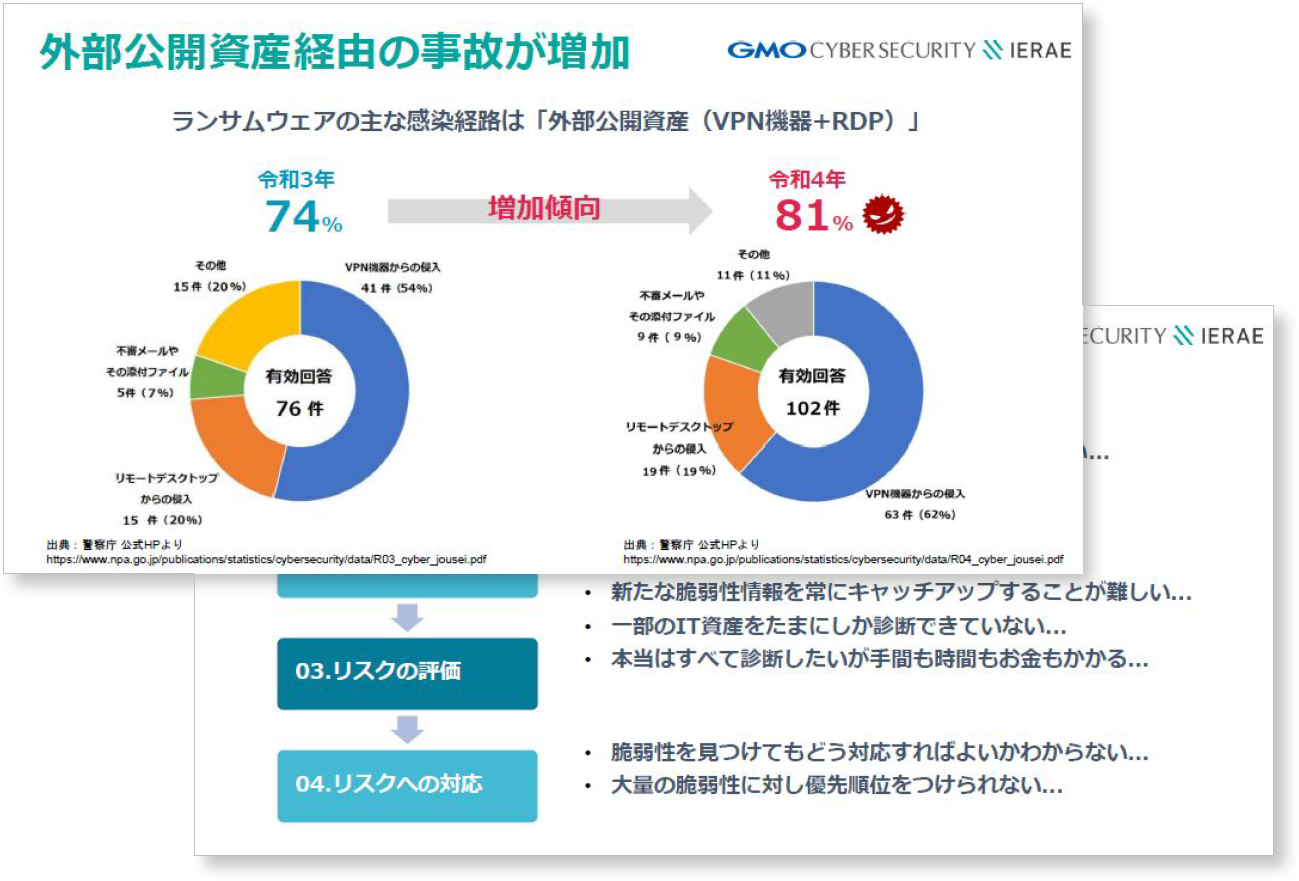
We provide materials that explain the fundamentals of ASM (Attack Surface Management) and the benefits of implementing its tools.













